A scene that revolves aroundOracleThe cloud services information security storm continues to heat up. Recently, a person who claimed to be rose87168Hackers who claim to have successfully hacked into Oracle CloudFederal Single Sign-On (SSO)The server, steal 600The company also sells the authentication data and encrypted passwords of 10,000 users on the dark web. Despite the fact that OracleOfficials deny hacking, but security media BleepingComputerThe data samples provided by the hacker were verified by various parties.
OracleCloud user data 'out of the box', hackers selling 6 million Oracle Cloud users on the dark web Source: Bleepingcomputer
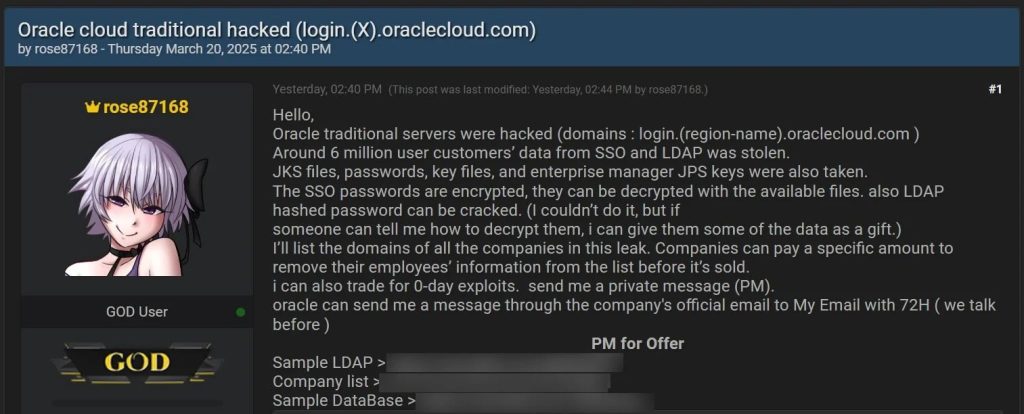
Last week, rose87168 made a high-profile claim on the Internet that it had hacked into Oracle Cloud's servers and obtained SSO and LDAP authentication data for 6 million users. The hacker even claimed that he could decrypt the encrypted passwords through the stolen files, and was willing to provide some data samples to those who were capable of recovering the data.
To substantiate their claims, the hackers have released a number of text files, including database contents, LDAP data, and a list of more than 140,000 enterprise domain names. It is worth mentioning that some of the domain names in the list seem to be test samples, and many enterprises have multiple domain names, which adds doubts to the authenticity of the relevant data.
What's even more shocking is that the hacker provided BleepingComputer with a link to Archive.org, a text file hosted on the login.us2.oraclecloud.com server, which clearly shows his email address. This means that the hackers not only stole data, but were even able to create files on Oracle's servers, which is conclusive evidence of their intrusion.
Oracle denies it, but the data validation is solid.
In the face of the hackers' provocation, Oracle responded quickly. On Friday, the company told BleepingComputer, "There was no breach of the Oracle Cloud, the publicly available authentication credentials did not come from the Oracle Cloud, and no customers suffered any data breaches or losses." The company took a very firm stance and refused to respond further to the incident.
However, BleepingComputer did not stop there. It obtained more data samples from the hackers and contacted relevant enterprises to verify the authenticity. The result was surprising: several companies confirmed, under the premise of anonymity, that the identifying information, including LDAP display names, email addresses, names, etc., matched their internal records, in sharp contrast to Oracle's "zero leakage" statement.
Email Exposure: Hackers and Oracle's 'Shadow Competition'
The hacker also disclosed to BleepingComputer his email communications with Oracle. One of the emails showed that rose87168 had proactively contacted Oracle's dedicated information security email to inform them of the intrusion in a straightforward manner: "I've delved deeper into your cloud dashboard infrastructure and found a serious vulnerability that allowed me to take full control of the data of 6 million users."
The content of the other e-mail was even more dramatic. The hacker claimed to have received a reply from a person using a ProtonMail ([@proton.me](@proton.me)) email address and claiming to be an Oracle employee: "We have received your email, please contact us via this email address in the future and reply when you receive it". However, since the identity of the sender and the authenticity of the email could not be verified, BleepingComputer has obscured the content. Whether the email conversation was unilaterally fabricated by the hacker, or whether there was indeed contact between the two parties, remains a mystery.
Root cause of vulnerability: outdated software?
An investigation by information security firm Cloudsek has brought more clues to the incident. The firm found that as of February 17, 2025, the login.us2.oraclecloud.com server was still running Oracle Fusion Middleware version 11g software, which has a CVE-2021-35587 vulnerability that could be exploited by an unauthenticated attacker to compromise Oracle Access Manager. Hackers claimed to have successfully exploited this vulnerability to compromise the server in question.
Ironically, Oracle took the server offline as soon as the incident came to light, as if tacitly recognizing that the problem did exist.
A Major Crisis in Cloud Security
At the heart of this controversy is the question of whether Oracle has really been compromised. If what the hackers say is true, the leakage of the authentication data of 6 million users would be a major disaster, and the number of companies affected and the scope of the impact would be staggering. Oracle's strong denial has also raised questions about whether it is trying to cover up the truth in order to protect its reputation.
For general users and enterprises, this is not only a technical competition, but also a test of trust in the security of cloud services. With the increasing popularity of cloud computing, it is hard to imagine the consequences of failing to protect the security of a technology giant, and Oracle needs to give more convincing explanations than just a vague "no leakage" statement.
Source:
https://www.bleepingcomputer.com/news/security/oracle-customers-confirm-data-stolen-in-alleged-cloud-breach-is-valid/
https://www.secrss.com/articles/77099


估計損失高達-19-億英鎊,為英國歷來之最.jpg)